DNS Security Extensions (DNSSEC) has been in the works for several years now but as of July 15th, 2010 (with little fanfare), the 13 name servers operating the root zone of the Internet’s Domain Name Servers (DNS) are now digitally signed with DNSSEC. So far DNSSEC is mostly being rolled out by government and financial institutions but many other web-facing entities may soon follow because of the perceived advantages. If you want to learn more specifically about how DNSSEC has been implemented at the root, check out http://www.root-dnssec.org/.
Up until recently, who.is has been my one-stop shop for records queries but when I query sites that I know have implemented DNSSEC, I can find no indication of this via who.is. I recently participated in a local DC chapter protocol study night and learned about a couple of new tools and other interesting things about DNSSEC.
www.dnsviz.com – Compliments of Sandia Labs we are provided with “A DNS visualization tool” (dnsviz). This allows you to view the public key of any given site that is using DNSSEC and shows you a flow chart of how the key is implemented. It will show you the line between trusted and untrusted portions of your target’s website and help diagnose issues if you are configuring DNSSEC for your own entity. I did find an interesting feature about this site. When you are the FIRST person to ever use this site to query a DNSSEC-enabled url, it will take a couple of minutes to spit back the response. Apparently I was the first person to think of querying bac.com. After the first time a site is queried, the results are spit back almost instantly for anyone else that queries it.
dig – Not to be confused with the ubiquitous social media tool digg (give this article some diggs if you’re a member ;-), the Domain Information Groper (Dig) is a command-line tool that allows you to do deep queries of DNS records and explicitly include the security extensions. It should be considered a replacement for nslookup. I found that it was already installed on OS X 10.6 by default but on my Gentoo VM I had to emerge bind to access the dig command. Dig will not give you the security extensions by default in either case. You will have to explicitly ask with a command such as:
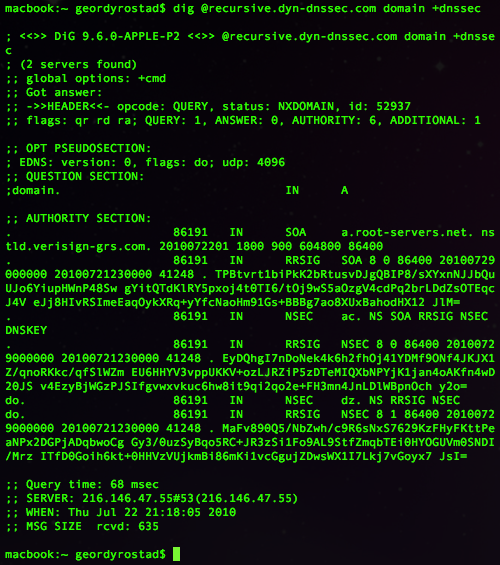
dig @recursive.dyn-dnssec.com domain +dnssec
This will return results similar to the following screencap:
For more information on DNSSEC, you can check out O’Reilly’s DNS and BIND. Here are some other relevant links for more information. If you only check one of the links below, make sure you read The Register’s take on DNSSEC since it gives you the quick overview of the situation.
- The Official, Unofficial, DNS Security Extensions (DNSSEC) Blog
- DNSSEC – DNS Security Extensions – Protocol Home Page
- The Register – Will DNSSEC kill your internet?
- Educause – 7 Things You Should Know About DNSSEC
If you like the content on this site, please support it by using this link to order from Amazon. You know you were going to go there and buy stuff anyhow so why not help me pay the hosting bill.