
I have a small stack of WRT54G routers at my house. When I find them second hand for cheap, they tend to be the WRT54G-TM variant. This version is actually great for modding and hacking because people seem to think it’s tied to T-Mobile so it must require a contract to use or something and they will sell them cheap. Personally I’ve had no trouble putting DD-WRT on the WRT54G-TM. In fact, the WRT54G-TM has 32MB ram and 8MB which is far more than most of the other routers in the series.
Today, I’m going to add a serial port to my WRT54G-TM so I can use a terminal to log into it. I think this will be handy for debugging since I plan to change the firmware on this router to Openwrt. I’m going to use a debugging board given to me by an unnamed friend at an unnamed company. There is nothing special about the board. It’s just a serial level shifter with a Maxim 3221CAE IC on it. It’s a fairly standard circuit that they publish on the datasheet for that IC. I’m just using this board because it will save me time doing this hack. The nice thing about the 3221 variant is that it will run on the 3.3V that is already present on the header. I’m loosely following directions from here showing two serial ports added to a WRT54GS.

To mark out the location for my new serial port, I’m going to use fire. I found a totally useless serial dock that corresponds with a defunct proprietary service and grabbed my blowtorch. I heated up the end of the cable as hot as I could get it and made an impression inside the WRT54G-TM. After that, I took a Dremel and routed out a hole for the DB9.

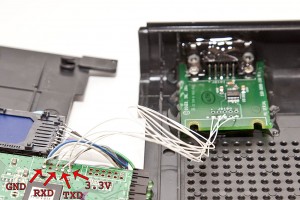
Next I soldered the wires in place. On the Maxim chip, the r-out goes to the RXD pin on the header and the t-in on the chip goes to the TXD on the header. 3.3V on the header goes to VCC on the chip and GND goes to GND. Make sure to leave the wires long enough to get the case closed again. After I was satisfied with the soldering, I globbed on a LOT of hot glue to hold that little serial board in place. Ignore my sd card mod since it’s not related to this hack.
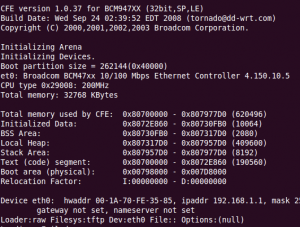
Once it was all back together I fired up Minicom with the settings 115,200, 8, 1, no parity and no flow control. The no flow control part is especially important. Now when I boot up the router, I can see all of the debugging information. Now with this serial port I can experiment with vlans and other things that can break your SSH session. If I wanted to get really tricky, I could probably even use my hacked WRT54G-TM as a wireless-serial bridge for consoling into my Cisco routers that I keep in the garage. They are too loud to keep by my desk.
If you like this article, you can support my site by using this link to buy your next WRT54G from Amazon. You might also consider buying Linksys WRT54G Ultimate Hacking
from Amazon. You might also consider buying Linksys WRT54G Ultimate Hacking for more advanced hardware and software hacks for your WRT54G.
for more advanced hardware and software hacks for your WRT54G.

routers this weekend. So far I have serial modded two out of the five that I have sitting here. The neat thing about the serial mod is that it’s so easy to grab a console off of it without worrying about network parameters. The bad thing is that your router may or may not be connected to the internet when you are on that console. It’s pretty easy to hook up to another wireless router in client mode from the console. I couldn’t find the following information all in one place so I’m going to hash out the quick version here:
after you’ve put an aftermarket root fs on it. All of these settings will disappear when you reboot your device aside from editing the resolv.conf although if you are using a WRT54G series router, your edits to the resolv.conf will also disappear.







